Delivering Unified Zero Trust Secure Networks
Today, a zero trust networking approach to security is paramount for organizations looking to build a robust cybersecurity program. Irrespective of which device, application, or user is accessing an enterprise resource, zero trust focuses on complete visibility and control over all activity on the network.
Arista’s zero trust networking principles, based on NIST 800-207, help customers address this challenge with three cornerstones: visibility, continuous diagnostics, and enforcement. The Arista NDR platform delivers continuous diagnostics for the entire enterprise threat landscape, processes countless points of data, senses abnormalities or threats, and reacts if necessary—all in a matter of seconds.

Intuitive dashboards to highlight the enterprise network threat landscape
The Arista solution stands out from traditional security because it is designed to mimic the human brain. It recognizes malicious intent and learns over time, giving defenders greater visibility and insight into what threats exist and how to respond to them. The solution enables security teams to:
Understand the Attack Surface
Get a clearer view and understanding of every user, device, and application—whether managed or unmanaged.
- See a complete view of the potential attack surface and associated business assets in the enterprise environment.
- Track every asset as it moves across the network while detecting malicious intent across entities.
- Watch the platform autonomously build an understanding of the relationships and similarities between entities.
Identify the threats others miss
Detect and understand the intent of network activities and enable the organization’s defenders to focus on the most consequential threats.
- Get an understanding of malicious intent for each entity by reviewing the cumulative evidence that is automatically correlated over time.
- Go beyond alerts and leverage the platform to autonomously investigate threats and enable security teams to visualize the entire incident kill chain across entities, protocols, and time.
- Automate threat hunts and build custom detection models for unique risks that enable security analysts to resolve threats contextually.
Deliver faster, more effective reaction
Access actionable information regarding the entities that pose the most business risk and respond effectively.
- Access comprehensive, descriptive, and investigative answers that give context to threats and event details.
- Provide forensic artifacts and timelines to equip defenders with meaningful evidence.
- Share insights with IT and security infrastructure teams to enhance existing investments.
Built to deploy in a few hours, Arista NDR enables organizations to further their zero trust journey. As Arista NDR integrates seamlessly with existing security investments, security teams can easily view high-risk incidents and compromised entities on a single pane of glass right from the start without the need for agents, manual configuration, or complex integrations.
Download the Arista NDR whitepaper to know more.
The Arista NDR Platform
Built-in sophistication and “thinking” ability that empowers organizations to successfully uncover and respond to zero day threats
The Arista NDR platform analyzes enterprise network traffic and autonomously identifies, assesses, and processes threats—giving actionable insights for the organization’s security teams to respond effectively.
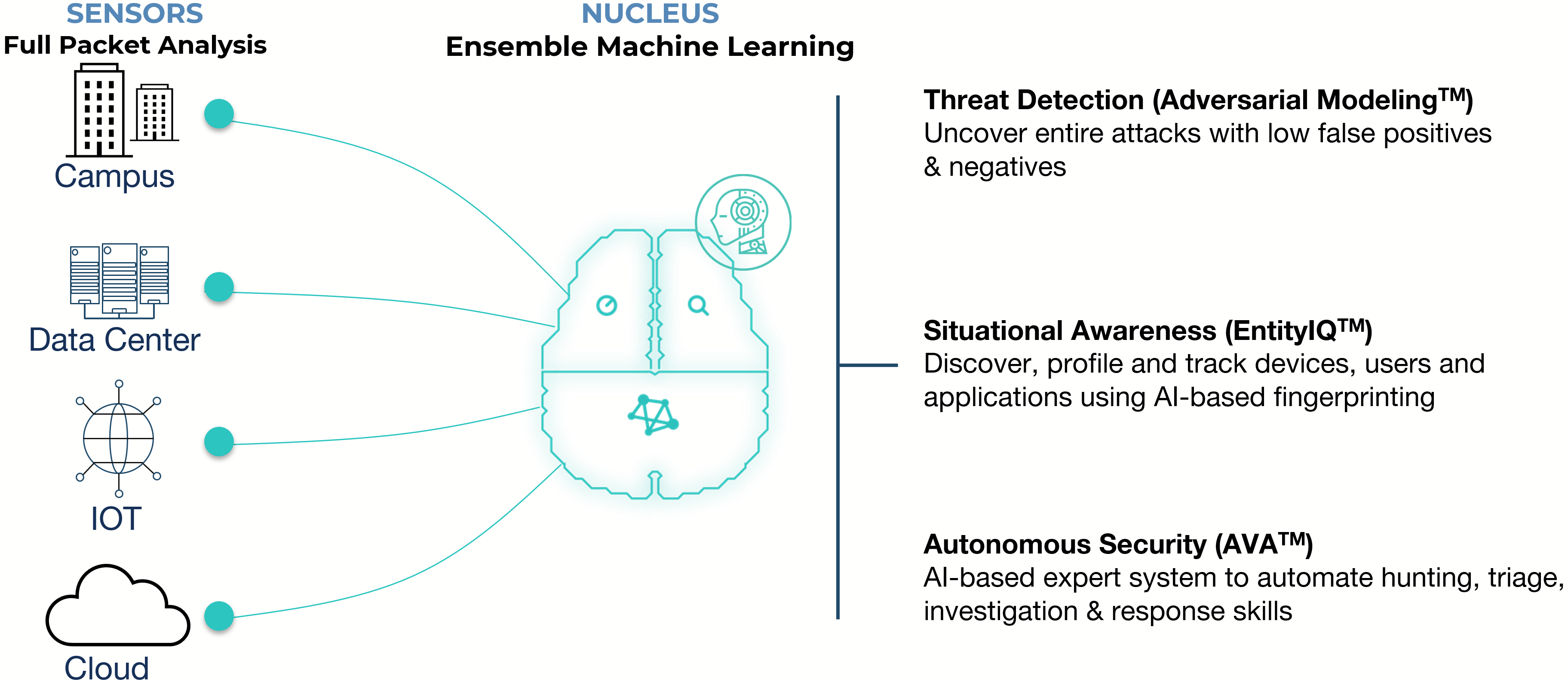
The platform that thinks before it acts
The Arista NDR platform deploys with:
- AVA Sensors: Get enhanced visibility and detailed traffic analysis from the core and perimeter to IoT and cloud.
- Continuously monitor enterprise devices, users, and applications wherever they are, even as IP addresses change while maintaining a forensic record of past activities.
- Deploy in a variety of form factors, including software on the network switch, standalone hardware, virtual or cloud, all without the need to deploy endpoint agents or complex integrations.
- Keep data at the point of collection to ensure privacy and compliance.
- AVA Nucleus: Turn information into action using artificial intelligence (AI), machine learning (ML), and human expertise.
- Understand the behaviors and attributes of entities across the network. Automatically monitor anomalies and unexplained changes across these entities.
- Detect malicious intent with low false positives and negatives through autonomous hunting for attacker tactics, techniques, and procedures.
- Lower SecOps costs with AI approaches including supervised and unsupervised ML, deep neural networks, belief propagation, multi-dimensional clustering, decision tree classification, and outlier detection.
- AVA AI: Leverage an AI-enabled decision support system that combines cloud scalability and codified expertise of real-world network security management experts
- Process ground-truth data about the state of devices on the enterprise network, including raw packets to pre-compute answers for questions a highly skilled analyst would ask.
- Use unsupervised and supervised ML to dynamically identify outliers based on deviations from peer group behaviors.
- Predict potential component failures, avoid false positives, and provide prescriptive recommendations to the operator to minimize network performance issues.

Arista NDR platform architecture
Discover the Arista NDR Advantage
Challenges in the Enterprise Threat Landscape
Connected technologies present new opportunities but also new vulnerabilities. Existing security solutions limit visibility, leaving the organization exposed to potential attacks. Continuously evolving cyber threats can no longer be mitigated by reactionary bolt-on security measures. Instead, organizations need security to permeate everything on the network today.
The Need for a Secure Network - not Network Security
Undetected Threats
Many modern threats blend in with business-justified activities. Traditional security tools focus on malware, letting many behavioral threats go undetected.
Narrow Insights
Traditional security systems do not connect the dots across the entire attack, instead leaving a trail of breadcrumbs that analysts have to piece together.
Increased Vulnerabilities
If the enterprise security team can’t see every threat, detect malicious intent, or get insights to respond effectively, the enterprise can become extremely vulnerable to cyberattacks.
How can an integrated approach to network security thwart zero day threats?
Organizations need holistic visibility across the entire enterprise attack surface for their security teams to effectively prioritize, hunt, and respond to zero day threats. A secure network solution provides comprehensive threat context and visibility into devices, users, and applications across the entire modern hybrid network infrastructure. This enables organizations to adopt a proactive approach to threat hunting and risk mitigation. And most importantly with Arista NDR, these capabilities are delivered using the very network switching infrastructure you already own, dramatically decreasing deployment time and operational overheads.
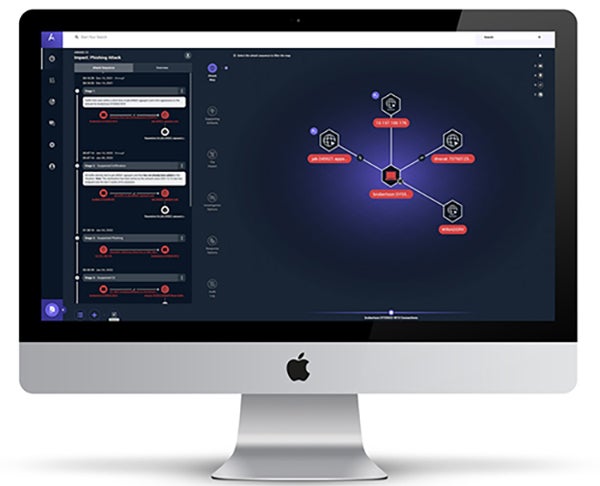
Understand the Entire Scope of an Attack
The Arista NDR Difference
A centralized platform that is built to capture, process, and store 100x more real-time network data through specialized AI-driven security detection and response workflows. The platform enables organizations to have a unified view of their security posture across hybrid networks.
EntityIQ™
A security knowledge graph to identify and profile all the devices, users, and applications on the enterprise network.
- Discover, characterize, track relationships, and cluster similar entities via behavioral fingerprints and several different AI techniques for more sophisticated threat analysis.
- Combine network data with behavioral and business data to increase an investigator’s situational awareness and efficiency of threat response.
- Use detailed graphical dashboards for a visual and textual map of detected threats and their targets backed by the latest threat intelligence.
AVA™ AI
The world’s first privacy-aware security decision support system to present end-to-end situations to security teams, rather than a plethora of meaningless alerts.
- Automate detection, triage, and investigations for quick, effective threat response across the dimensions of time, entities, and protocols, on a single pane of glass.
- Access Arista’s threat research, hunting, forensics, and investigative expertise embedded in an AI-driven platform that detects mal-intent or potential threats.
- Benefit from federated machine learning that ensures customer data stays firmly inside the enterprise infrastructure.
Adversarial Modeling™
A building-block approach to easily express even the most complex attacker tactics, techniques, and procedures.
- Benefit from an unparalleled interactive language to look at the abstract, inferred information about the environment, event-oriented activity records, low-level raw packets, and more.
- Use multi-dimensional modeling to connect dots across time, protocols, entity behaviors, and kill-chain stage automating detections that today require threat hunting expertise.
- Autonomously pull open-source and threat intelligence and thus, contextualize a potential threat uncovered in the environment.
To know more, download the datasheet.
Datasheets & Guides
- .Arista NDR Datasheet
- .Arista NDR Campus Edition Datasheet
- .Integrated Security Operations: Arista NDR with Zscaler
- .Awake Labs Deployment & Integration Services
- .Microsoft Sentinel + Arista NDR Datasheet
- .Intelligent Observability and Security Operations with Arista DANZ Forensic Exchange Solution Guide
- .Arista NDR Covers the Spectrum of the MITRE ATT&CK Framework Datasheet
- .The Power of Integrated Network & Endpoint Detection and Response Datasheet (CrowdStrike)
- .The Power of Integrated Network & Endpoint Detection and Response Datasheet (SentinelOne)
White Papers
- .Arista NDR White Paper
- .Arista Zero Trust Security for Cloud Networking
- .Network Traffic Analysis: To Decrypt or Not to Decrypt
- .Awake Security opens the eyes of security operations personnel
- .Building Your Zero Trust Strategy with NIST 800-207 and Arista NDR
- .EMA Radar™ Summary for Network-Based Security Analytics: Q3 2018
- .EMA Top 3 Report and Decision Guide for Security-Analytics
- .Frost and Sullivan Best Practices Award for NTA
- .Sans SOC Survey
- .Survey SOC 2018 AwakeSecurity
- .Securing Against Ransomware Through MITRE ATT&CK– It’s Too Late If They Exfiltrate
- .TAG Cyber Special Edition: ADVANCED DATA-DRIVEN NETWORK SECURITY
- .The 5 Levels of Autonomous Security: What level are you?
- .Tenets of a Healthy Hospital Infrastructure
- .The Advent of Advanced Network Detection and Response and Why it Matters
- .Tag Cyber Annual Market And Industry Insights
- .The Network at the Core of Detection and Response
- .The Seven Habits of Highly Effective Security Teams
- .The State of Cybersecurity Incident Response
- .Threat Detection And Response Landscape
- .Tolly Network Detection Response Evaluation Darktrace
- . Top 4 Roadblocks to SOC Productivity
- .Buyer’s Guide: Network Detection and Response (NDR)
- .Implementing CIS Controls Version 8 with Arista NDR
Case Studies
- .Employee Selling Corporate Secrets
- .Spear Phishing Detection and Intelligent Response
- .Contractor Using Security Cameras to Spy
- .Following the Trail of a Spear Phishing Campaign
- .IoT Devices Exfiltrating Data
- .Malicious Browser Extensions
- .Ransomware Attack Unfolds
- .Russian-made Remote Desktop Software Installed on Critical Infrastructure
- .Serverless C2 in the Cloud
- .Tapping IP Phones In Sensitive Locations
- .Unauthorized VPN Used to Hide Data Exfiltration
- .Awake Security Demonstration
- .Artificial Intelligence and Security – Separating The Hype from Reality
- .The Power of Integrated Network & Endpoint Detection and Response
- .Network Detection and Response Demo – Awake in 3 Minutes
- .Innovate 2021 – Security Roundtable
- .Detecting Threats like Sunburst / SolarWinds / Solorigate
- .TAG Cyber interviews Rahul Kashyap on the Technical Aspects of the New Network
- .TAG Cyber interviews Rahul Kashyap on the Business Problems & Challenges of the New Network
- .Arista NDR Explainer
Webinars