MPLS
MPLS Overview
Multiprotocol Label Switching (MPLS) provides a networking process that replaces complete network addresses with short path labels for directing data packets to network nodes. The labels identify virtual links (paths) between distant nodes rather than endpoints. MPLS is scalable and protocol-independent. MPLS assigns labels to data packets and uses the labels to determine packet forwarding destinations without examining the packet.
Arista switches utilize MPLS to improve efficiency and control from servers through data centers and the WAN. The MPLS implementation supports manually configured static MPLS tunneling on each switch or established over a network by an SDN Controller. The configuration specifies a set of rules that filter packets based on matching criteria. Each rule applies MPLS-related actions to packets that match the rule criteria. Each rule includes a metric that the switch uses to select an action when multiple rules match a packet.
MPLS Implementation
- A 20-bit value compared to the top header label of each MPLS packet. Other rule parameters may be applied to packets with matching top-label values.
- A next hop location that specifies the packet’s next destination, IPv4 or IPv6, and the interface through which the switch forwards the packet.
- An MPLS label stack management action performed on filtered packets:
- pop-payload -Removes the top label from the stack and terminates an Label-Switched Path (LSP).
- swap-label -Replaces the top label with a specified new label and passes a packet along an LSP.
- A rule metric to select a rule when multiple rules match an MPLS packet.
The switch drops packets that do not match any MPLS rules.
MPLSoGRE Filtered Mirroring
In MPLS over Generic Routing Encapsulation (MPLSoGRE) filtered mirroring, IPv4 over MPLS over GRE and IPv6 over MPLS over GRE packets that enter a GRE tunnel endpoint where MPLS performs a lookup, and selects packets for mirroring based on the destination IP address field in the inner IPv4 or IPv6 header.
The header has the following format for the packets selected for mirroring:
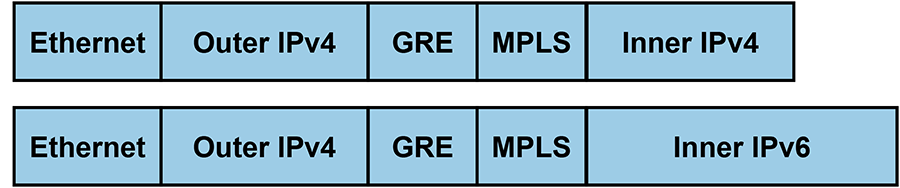
When mirroring to a GRE tunnel, the payload of the outgoing GRE packet contains the payload of the incoming source packet starting from the MPLS header. EOS strips L2 and outer L3 headers from the mirror copy. When the MPLS lookup fails, the packet becomes eligible for mirroring based on the selection criteria defined in the ACL.
Mixed TTL/DSCP in MPLS Tunnel Termination
A Label Edge Router (LER) decapsulating an MPLS packet may choose to source the TTL and DSCP fields from either the MPLS header or the original inner IPv4 header. However, some applications need the TTL field value from the MPLS header, while retaining the DSCP from the original IPv4 header. Mixed TTL/DSCP in MPLS Tunnel Termination enables tunnel termination to select this specific mix of two modes.
Configuring Mixed TTL/DSCP in MPLS Tunnel Termination
switch(config)# mpls ip
switch(config)# mpls static vrf-label mpls-label vrf vrf-name
switch(config)# ip routing vrf vrf-nameswitch(config)# mpls tunnel termination model ttl uniform dscp pipeswitch(config)# hardware tcam
# May use any profile that provides “qos ip”
switch(config-tcam)# profile name copy default
switch(config-tcam-profile-name)# feature qos ip
switch(config-tcam-profile-name-feature-qos-ip)# packet mpls ipv4 forwarding routed decap
switch(config-tcam)# system profile name Packet Support for IPv6
switch(config)# hardware tcam
# May use any profile that provides “qos ipv6”
switch(config-tcam)# profile name copy default
switch(config-tcam-profile-name)# feature qos ipv6
switch(config-tcam-profile-name-ipv4)# packet mpls ipv6 forwarding routed decap
switch(config-tcam)# system profile nameSupport for MPLS Packets in IP ACLs
Ingress and egress IPv4 and IPv6 access-lists do not automatically match the inner IP header when processing IP over MPLS traffic.
EOS supports matching of the inner IP header in an access-list by adding the proper packet types to the corresponding TCAM features.
DSCP-to-TC Maps for MPLS Traffic to Layer 3 VRFs
MPLS-labeled traffic, both IPv4 and IPv6, can be decapsulated and routed using a specific VRF, either the default or a named VRF. The MPLS label can be statically assigned to a specific VRF, or dynamically through L3 EVPN MPLS. In this configuration, the switch adds a traffic class label based on a packet's ingress DSCP to the decapsulated MPLS packet if directed to a specific VRF. This provides an MPLS tunneling technique called Short Pipe Mode.
A QoS map steers the mapping of DSCP labels to a traffic class. Up to 10 custom maps can be applied. A map only uses hardware resources when attached to at least one VRF. When first creating a map, the DSCP-to-TC map copies the configuration from the global map, and subsequent changes to the global map do not have any effect on custom maps.
Configuring MPLS
Enable MPLS routing using the mpls ip command.
switch(config)# mpls ip
switch(config)# show running-config mpls ip
!
end
switch(config)#The mpls static command creates MPLS rules. MPLS static rules identify a set of MPLS packets by a common top label and defines the method of handling these packets.
Use the following commands to create an MPLS rule that matches packets with a top label value of 3400 and causes the removal of the top label from the header stack. Configure the next hop destination of the IPv4 payload as the IPv4 address 10.14.4.4 using the interface ethernet 3/3/3. This rule has a metric value of 100.
switch(config)# mpls static top-label 3400 ethernet 3/3/3 10.14.4.4 pop payload-type ipv4
switch(config)# show running-config
!
mpls static top-label 3400 Ethernet3/3/3 10.14.4.4 pop payload-type ipv4
!
end
switch(config)#These commands create a backup rule that forwards the packet through interface ethernet 4/3. This rule’s metric value of 150 assigns it backup status prior to the first rule.
switch(config)# mpls static top-label 3400 ethernet 4/3 10.14.4.4 pop payload-type ipv4 metric 150
switch(config)# show running-config
!
mpls static top-label 3400 Ethernet4/3 10.14.4.4 pop payload-type ipv4 metric 150
mpls static top-label 3400 Ethernet3/3/3 10.14.4.4 pop payload-type ipv4
!
end
switch(config)#Create an MPLS rule that forwards the packet to the nexthop address through any interface:
switch(config)# mpls static top-label 4400 10.15.46.45 pop payload-type ipv4
switch(config)# show running-config
!
mpls static top-label 3400 Ethernet4/3 10.14.4.4 pop payload-type ipv4 metric 150
mpls static top-label 3400 Ethernet3/3/3 10.14.4.4 pop payload-type ipv4
mpls static top-label 4400 10.15.46.45 pop payload-type ipv4
!
end
switch(config)#Configure a static tunnel for the tunnel endpoint 64.0.0.1 and add a label 11111 to it.
switch(config)# mpls static STATIC 64.0.0.1/32 54.0.0.1 Port-Channel7 label-stack 11111The following example shows an MPLS swap route configuration. The following command swaps a packet with MPLS top label 3400 to 5600 for forwarding to 10.14.4.4.
switch(config)# mpls static top-label 3400 10.14.4.4 swap 5600
switch(config)#The following example shows MPLS next-hop groups configuration for MPLS. The following commands configures the specification of a next hop group called TestGrp1 with two entries.
switch(config)# nexthop-group TestGrp1 type MPLS
switch(config-nexthop-group-TestGrp1)# size 2
switch(config-nexthop-group-TestGrp1)# entry 0 push label-stack 70 nexthop 10.20.30.5
switch(config-nexthop-group-TestGrp1)# entry 1 push label-stack 71 nexthop 10.20.30.6
switch(config-nexthop-group-TestGrp1)# exit
switch(config)#The label-stack parameter accepts only one label. Tunnel-source and ttl commands do not apply to MPLS NexthopGroups. The nexthop entry resolves when the entry specifies a remote next hop. The show command indicates the resolved, directly-attached nexthop.
Display the switch’s MPLS static rule configuration for specified routes and rules using the show mpls route.
switch# show mpls config route
In-Label Out-Label Metric Payload NextHop
3400 pop 100 ipv4 10.14.4.4,Et3/3/3
3400 pop 150 ipv4 10.14.4.4,Et4/3
switch#Display statistics about the configuration and implementation of MPLS rules using the show mpls route summary command.
switch# show mpls route summary
Number of Labels: 1 (1 unprogrammed)
Number of adjacencies in hardware: 0
Number of backup adjacencies: 2
switch#The show mpls lfib route command displays the Label Forward Information Base of the switch.
switch(config)# show mpls lfib route
MPLS forwarding table (Label [metric] Vias) - 1 routes
MPLS next-hop resolution allow default route: False
Via Type Codes:
M - MPLS via, P - Pseudowire via,
I - IP lookup via, V - VLAN via,
VA - EVPN VLAN aware via, ES - EVPN ethernet segment via,
VF - EVPN VLAN flood via, AF - EVPN VLAN aware flood via,
NG - Nexthop group via
Source Codes:
G - gRIBI, S - Static MPLS route,
B2 - BGP L2 EVPN, B3 - BGP L3 VPN,
R - RSVP, LP - LDP pseudowire,
L - LDP, M - MLDP,
IP - IS-IS SR prefix segment, IA - IS-IS SR adjacency segment,
IL - IS-IS SR segment to LDP, LI - LDP to IS-IS SR segment,
BL - BGP LU, ST - SR TE policy,
DE - Debug LFIB
S 300 [100]
via M, 192.0.2.2, swap 500
payload mpls, bypass egress-acl
interface Ethernet3/1
switch(config)#The show ip route command displays all IP routes along with static MPLS push routes and Next hop Group routes.
switch(config)# show ip route
VRF name: default
Codes: C - connected, S - static, K - kernel,
O - OSPF, IA - OSPF inter area, E1 - OSPF external type 1,
E2 - OSPF external type 2, N1 - OSPF NSSA external type 1,
N2 - OSPF NSSA external type2, B I - iBGP, B E - eBGP,
R - RIP, I L1 - ISIS level 1, I L2 - ISIS level 2,
O3 - OSPFv3, A B - BGP Aggregate, A O - OSPF Summary,
NG - Nexthop Group Static Route, V - VXLAN Control Service
Gateway of last resort is not set
C 192.0.2.0/24 is directly connected, Ethernet1/1
S 3.3.3.0/24 [1/0] via 192.0.2.2, Ethernet1/1 label 200
S 10.80.0.0/13 [1/0] via 172.24.0.1, Management1
S 10.95.0.0/20 [1/0] via 172.24.0.1, Management1
C 172.24.0.0/18 is directly connected, Management1
S 172.16.0.0/12 [1/0] via 172.24.0.1, Management1
switch(config)#The MPLS push routes are static routes so the show ip route static command also displays the output for an MPLS Nexthop Group assuming there is a route pointing to the NexthopGroup and the entries in the NexthopGroup are resolved. The output displays the information for show nexthop-group TestGrp1, the test group configured earlier.
switch(config)# show nexthop-group TestGrp1
TestGrp1
Id 2
Type MPLS
Size 2
Entries
0 push label-stack 70 nexthop 10.20.30.5
Tunnel destination directly connected, Ethernet2
52:14:a3:a6:50:e8, Ethernet2
1 push label-stack 71 nexthop 10.20.30.6
Tunnel destination directly connected, Ethernet2
52:14:a3:a6:50:e8, Ethernet2
switch(config)#LSP Ping/Traceroute for MPLS Nexthop Group Tunnels
The ping/traceroute mpls tunnel nexthop-group command checks the liveness of Nexthop Group tunnel endpoint for an MPLS Nexthop Group.
The following displays the output for the ping command when specifying the endpoint.
switch(config)# rtrmpls1
switch(config-rtrmpls1)# ping mpls tunnel nexthop-group 100.0.116.1/32
LSP ping to nexthop-group tunnel 100.0.116.1/32
100.0.116.1/32: nexthop-group tunnel index 1 (nexthop-group name: nhg-100)
Entry 0
Via 10.0.16.2
Reply from 10.0.108.1: seq=1, time=507.546ms
Entry 1
Via 10.0.16.8
Reply from 10.0.113.1: seq=1, time=516.131ms
--- nexthop-group tunnel index 1, nexthop-group nhg-100: lspping statistics
---
Entry 0
Via 10.0.16.2
1 packets transmitted, 1 received, 0% packet loss, time 652ms
1 received from 10.0.108.1, rtt min/max/avg 507.546/507.546/507.546 ms
Entry 1
Via 10.0.16.8
1 packets transmitted, 1 received, 0% packet loss, time 652ms
1 received from 10.0.113.1, rtt min/max/avg 516.131/516.131/516.131msThe following displays the output when specifying the endpoint in the traceroute command.
switch(config)# rtrmpls1
switch(config-rtrmpls1)# traceroute mpls tunnel nexthop-group 100.0.116.1/32
LSP traceroute to nexthop-group tunnel 100.0.116.1/32
Traceroute over nexthop-group tunnel index 1, nexthop-group nhg-100 Entry 1
Entry 1
1 10.0.225.1 32.571ms
label stack (top label first): 89
2 10.0.227.1 42.866ms
label stack (top label first): 109
3 10.0.229.1 54.893ms
label stack (top label first): 110
4 10.0.231.1 15.946ms
label stack (top label first): 111
5 10.0.233.1 27.72ms
label stack (top label first): 112
6 10.0.113.1 36.383msThe following displays the output for the ping command where the static route resolves over Nexthop Group tunnel(s).
switch(config-rtrmpls1)# ping mpls static ip 100.0.77.0/24
LSP ping to static MPLS push label route 100.0.77.0/24
100.0.77.0/24: nexthop-group tunnel index 1 (nexthop-group name: nhg-46)
Entry 0
Via 10.0.25.5
Reply from 10.0.51.1: seq=1, time=112.171ms
100.0.77.0/24: nexthop-group tunnel index 2 (nexthop-group name: nhg-64)
Entry 0
Via 10.0.25.4
Reply from 10.0.68.1: seq=1, time=121.809ms
Entry 1
Via 10.0.25.9
Reply from 10.0.76.1: seq=1, time=133.668ms
--- nexthop-group tunnel index 1, nexthop-group nhg-46: lspping statistics ---
Entry 0
Via 10.0.25.5
1 packets transmitted, 1 received, 0% packet loss, time 251ms
1 received from 10.0.51.1, rtt min/max/avg 112.171/112.171/112.171 ms
--- nexthop-group tunnel index 2, nexthop-group nhg-64: lspping statistics ---
Entry 0
Via 10.0.25.4
1 packets transmitted, 1 received, 0% packet loss, time 251ms
1 received from 10.0.68.1, rtt min/max/avg 121.809/121.809/121.809 ms
Entry 1
Via 10.0.25.9
1 packets transmitted, 1 received, 0% packet loss, time 251ms
1 received from 10.0.76.1, rtt min/max/avg 133.668/133.668/133.668 msThe following displays the output for the traceroute command where the static route resolves over Nexthop Group tunnel(s). The command randomly selects a tunnel.
switch(config-rtrmpls1)# traceroute mpls static ip 100.0.77.0/24LSP traceroute to 100.0.77.0/24
100.0.77.0/24: nexthop-group tunnel index 1 (nexthop-group name: nhg-46)
100.0.77.0/24: nexthop-group tunnel index 2 (nexthop-group name: nhg-64)
Traceroute over nexthop-group tunnel index 1, nexthop-group nhg-46 Entry 0
Entry 0
1 10.0.83.1 382.798ms
label stack (top label first): 35
2 10.0.85.1 42.7ms
label stack (top label first): 47
3 10.0.87.1 55.815ms
label stack (top label first): 48
4 10.0.89.1 17.728ms
label stack (top label first): 49
5 10.0.91.1 29.452ms
label stack (top label first): 50
6 10.0.51.1 38.686msConfiguring Egress IPv4 and IPv6 over MPLS ACLs
By default, IPv4 and IPv6 over MPLS packets use ACLs at the egress stage by default, applicable only to IPv4 and IPv6 over MPLS packets with a popped MPLS label. Override this behavior if required by disabling egress ACLs for certain MPLS labels. The switch does not require a special configuration to enable egress ACLs on IPv4 and IPv6 over MPLS packets.
-
This command disables egress ACLs for MPLS top-label 12000 on the egress interface 120.1.1.1 next hop address.
switch(config)# no mpls static top-label 12000 120.1.1.1 pop payload-type ipv6 switch(config)# -
This command enables egress ACLs for MPLS top-label 12000 on the egress interface 120.1.1.1 next hop address.
switch(config)# mpls static top-label 12000 120.1.1.1 pop payload-type ipv6 switch(config)#
Configuring MPLSoGRE Filtered Mirroring
Configure the filtered mirroring of terminated MPLSoGRE packets by creating an IPv4 access list, and then attaching the IPv4 access list to a monitor session source with a tunnel decap group. This IPv4 access-list has rules that match to either inner IPv4 or IPv6 destination addresses.
Enabling the TC-Counters TCAM Profile
- EOS does not enforce security ACLs on IPv4oMPLSoGRE and IPv6oMPLSoGRE terminated packets.
- Set the rules of a mirroring-ACL to match either inner IPv4 or inner IPv6 header fields, but not both.
The ACLs containing rules to match both inner IPv4 and inner IPv6 header fields do not apply to a single source interface in multiple mirroring sessions. In other words, all ACLs applied to a shared source interface must contain either inner IPv4 rules or inner IPv6 rules.
switch(config)# hardware tcam
switch(config-hw-tcam)# system profile tc-counters
switch(config-hw-tcam)# exitDefining Two IPv4 Access-Lists
The ip access-list command places the switch in ACL configuration mode, a group change mode that modifies an IPv4 access control list. The command specifies the name of the IPv4 ACL that subsequent commands modify and creates an ACL if it references a nonexistent list. All changes in a group change mode edit session are pending till the end of the session.
switch(config)# ip access-list dIPv4
switch(config)# 10 permit ip any any inner ip any host 5.5.5.5
switch(config)# exit
switch(config)# ip access-list dIPv6
switch(config)# 10 permit ip any any inner ipv6 any host 55::55
switch(config)# exitAttaching Access-Lists
switch(config)# monitor session sess1 source et1 rx ip access-group dIPv4
switch(config)# monitor session sess1 destination tunnel mode gre source 1.1.1.1 destination 2.2.2.2
switch(config)# monitor session sess2 source et2 rx ip access-group dIPv6
switch(config)# monitor session sess2 destination tunnel mode gre source 3.3.3.3 destination 4.4.4.4
switch(config)# show monitor session
Session sess1
------------------------
Source Ports:
Rx Only: Et1(IP ACL: dIPv4)
Destination Ports:
status source dest TTL DSCP proto VRF fwd-drop
Gre1 : active 1.1.1.1 2.2.2.2 128 0 0x88be default no
Session sess2
------------------------
Source Ports:
Rx Only: Et2(IP ACL: dIPv6), Et5(IP ACL: dIPv6)
Destination Ports:
status source dest TTL DSCP proto VRF fwd-drop
Gre2 : active 3.3.3.3 4.4.4.4 128 0 0x88be default no
switch(config)#Configuring Support IP ACLs for MPLS Packets
Configuring Ingress IP Access Control (ACL) List Support
packet mpls ipv4 forwarding bridged
packet mpls ipv4 forwarding mplsThe ingress inner IP header matching creates a user-defined profile with these new packet types. Although MAC access-lists do not match on the inner IP header, you must add this packet type in order to generate a lookup for MPLS packets if using MAC ACLs.
switch(config)# hardware tcam
switch(config-tcam)# profile MyMPLS copy default
switch(config-tcam-profile-MyMPLS)# feature acl port ip
switch(config-tcam-feature-acl-port-ip)# packet mpls ipv4 forwarding bridged
switch(config-tcam-feature-acl-port-ip)# packet mpls ipv4 forwarding mpls
switch(config-tcam-feature-acl-port-ip)# exit
switch(config-tcam-profile-MyMPLS)# feature acl port ipv6
switch(config-tcam-feature-acl-port-ipv6)# packet mpls ipv6 forwarding bridged
switch(config-tcam-feature-acl-port-ipv6)# packet mpls ipv6 forwarding mpls
switch(config-tcam-profile-MyMPLS)# feature acl port mac
switch(config-tcam-feature-acl-port-mac)# packet mpls ipv4 forwarding bridged
switch(config-tcam-feature-acl-port-mac)# packet mpls ipv4 forwarding mpls
switch(config-tcam-feature-acl-port-mac)# packet mpls ipv6 forwarding bridged
switch(config-tcam-feature-acl-port-mac)# packet mpls ipv6 forwarding mplsEOS supports ingress on inner IP header matching in MPLS packets on PBR ACLs. To enable this, the following must be configured in a user-defined TCAM profile:
switch(config-tcam)profile pbr-acls copy default
switch(config-tcam-profile-pbr-acls)# feature pbr mpls
switch(config-tcam-feature-pbr-mpls)# packet ipv4 forwarding mpls
switch(config-tcam-feature-pbr-mpls)# exit
switch(config-tcam-profile-pbr-acls)# feature pbr mpls
switch(config-tcam-feature-pbr-mpls)# packet mpls ipv6 forwarding mplsConfiguring Egress IPv4 and IPv6 over MPLS ACLs
By default, IPv4 and IPv6 over MPLS packets use ACLs at the egress stage by default, applicable only to IPv4 and IPv6 over MPLS packets with a popped MPLS label. Override this behavior if required by disabling egress ACLs for certain MPLS labels. The switch does not require a special configuration to enable egress ACLs on IPv4 and IPv6 over MPLS packets.
-
This command disables egress ACLs for MPLS top-label 12000 on the egress interface 120.1.1.1 next hop address.
switch(config)# no mpls static top-label 12000 120.1.1.1 pop payload-type ipv6 switch(config)# -
This command enables egress ACLs for MPLS top-label 12000 on the egress interface 120.1.1.1 next hop address.
switch(config)# mpls static top-label 12000 120.1.1.1 pop payload-type ipv6 switch(config)#
Configuring MPLS Pop Terminated Packets
switch(config)# hardware tcam
switch(config-tcam)# profile MyMPLS
switch(config-tcam-profile-MyMPLS)# feature acl port ip packet egress mpls-tunnelled-match
switch(config-tcam-feature-acl-port-ip-egress-mpls-tunnelled-match)#switch(config)# hardware tcam
switch(config-tcam)# profile egress-mpls copy MyMPLSConfiguring MPLS VRF-Decapsulated Packets
switch(config)# hardware tcam
switch(config-tcam)# profile VRF-Decap copy default
switch(config-tcam-profile-VRF-Decap)# feature qos ip packet mpls ipv4 forwarding routed decapSupporting Traffic Policy on Interfaces
Access Control Lists (ACL) configures the action for packets traversing the packet processor pipeline based on different fields of packets. Usually, this requires the TCAM to match packets with multiple entries matching the list of IP addresses. The TCAM has limited resources, so traffic-policy performs transformation of the fields of the packet, and summarizes them in terms of the relevant rules this field matches by using command interface traffic-policy.
Custom TCAM Profile
switch(config)# hardware tcam
switch(config-tcam)# profile traffic-policy
switch(config-tcam-profile-traffic-policy)# feature acl port mac
switch(config-tcam-feature-acl-port-mac)# sequence 55
switch(config-tcam-feature-acl-port-mac)# key size limit 160
switch(config-tcam-feature-acl-port-mac)# key field dst-mac ether-type src-mac
switch(config-tcam-feature-acl-port-mac)# action count drop
switch(config-tcam-feature-acl-port-mac)# packet ipv4 forwarding bridged
switch(config-tcam-feature-acl-port-mac)# packet ipv4 forwarding routed
switch(config-tcam-feature-acl-port-mac)# packet ipv4 forwarding routed multicast
switch(config-tcam-feature-acl-port-mac)# packet ipv4 mpls ipv4 forwarding mpls decap
switch(config-tcam-feature-acl-port-mac)# packet ipv4 mpls ipv6 forwarding mpls decap
switch(config-tcam-feature-acl-port-mac)# packet ipv4 non-VXLAN forwarding routed decap
switch(config-tcam-feature-acl-port-mac)# packet ipv4 VXLAN forwarding bridged decap
switch(config-tcam-feature-acl-port-mac)# packet ipv6 forwarding bridged
switch(config-tcam-feature-acl-port-mac)# packet ipv6 forwarding routed
switch(config-tcam-feature-acl-port-mac)# packet ipv6 forwarding routed decap
switch(config-tcam-feature-acl-port-mac)# packet ipv6 forwarding routed multicast
switch(config-tcam-feature-acl-port-mac)# packet ipv6 ipv6 forwarding routed decap
switch(config-tcam-feature-acl-port-mac)# packet mpls forwarding bridged decap
switch(config-tcam-feature-acl-port-mac)# packet mpls ipv4 forwarding mpls
switch(config-tcam-feature-acl-port-mac)# packet mpls ipv6 forwarding mpls
switch(config-tcam-feature-acl-port-mac)# packet mpls non-ip forwarding mpls
switch(config-tcam-feature-acl-port-mac)# packet non-ip forwarding bridged
switch(config-tcam-feature-acl-port-mac)# exit
switch(config-tcam-profile-traffic-policy)# feature forwarding-destination mpls
switch(config-tcam-feature-forwarding-destination-mpl)# sequence 100
switch(config-tcam-feature-forwarding-destination-mpl)# exit
switch(config-tcam-profile-traffic-policy)# feature mirror ip
switch(config-tcam-feature-mirror-ip)# sequence 80
switch(config-tcam-feature-mirror-ip)# key size limit 160
switch(config-tcam-feature-mirror-ip)# key field dscp dst-ip ip-frag ip-protocol l4-dst-port l4-ops l4-src-port src-ip tcp-control
switch(config-tcam-feature-mirror-ip)# action count mirror set-policer
switch(config-tcam-feature-mirror-ip)# packet ipv4 forwarding bridged
switch(config-tcam-feature-mirror-ip)# packet ipv4 forwarding routed
switch(config-tcam-feature-mirror-ip)# packet ipv4 forwarding routed multicast
switch(config-tcam-feature-mirror-ip)# packet ipv4 non-VXLAN forwarding routed decap
switch(config-tcam-feature-mirror-ip)# exit
switch(config-tcam-profile-traffic-policy)# feature mpls
switch(config-tcam-feature-mpls)# sequence 5
switch(config-tcam-feature-mpls)# key size limit 160
switch(config-tcam-feature-mpls)# action drop redirect set-ecn
switch(config-tcam-feature-mpls)# packet ipv4 mpls ipv4 forwarding mpls decap
switch(config-tcam-feature-mpls)# packet ipv4 mpls ipv6 forwarding mpls decap
switch(config-tcam-feature-mpls)# packet mpls ipv4 forwarding mpls
switch(config-tcam-feature-mpls)# packet mpls ipv6 forwarding mpls
switch(config-tcam-feature-mpls)# packet mpls non-ip forwarding mpls
switch(config-tcam-feature-mpls)# exit
switch(config-tcam-profile-traffic-policy)# feature-pbr-ip
switch(config-tcam-feature-pbr-ip)# sequence 60
switch(config-tcam-feature-pbr-ip)# key size limit 160
switch(config-tcam-feature-pbr-ip)# key field dscp dst-ip ip-frag ip-protocol l4-dst-port l4-ops-18b l4-src-port src-ip tcp-control
switch(config-tcam-feature-pbr-ip)# action count redirect
switch(config-tcam-feature-pbr-ip)# packet ipv4 forwarding routed
switch(config-tcam-feature-pbr-ip)# packet ipv4 mpls ipv4 forwarding mpls decap
switch(config-tcam-feature-pbr-ip)# packet ipv4 mpls ipv6 forwarding mpls decap
switch(config-tcam-feature-pbr-ip)# packet ipv4 non-VXLAN forwarding routed decap
switch(config-tcam-feature-pbr-ip)# packet ipv4 VXLAN forwarding bridged decap
switch(config-tcam-feature-pbr-ip)# exit
switch(config-tcam-profile-traffic-policy)# feature-pbr-ipv6
switch(config-tcam-feature-pbr-ipv6)# sequence 30
switch(config-tcam-feature-pbr-ipv6)# key field dst-ipv6 ipv6-next-header l4-dst-port l4-src-port src-ipv6-high src-ipv6-low tcp-control
switch(config-tcam-feature-pbr-ipv6)# action count redirect
switch(config-tcam-feature-pbr-ipv6)# packet ipv6 forwarding routed
switch(config-tcam-feature-pbr-ipv6)# exit
switch(config-tcam-profile-traffic-policy)# feature pbr mpls
switch(config-tcam-feature-pbr-mpls)# sequence 65
switch(config-tcam-feature-pbr-mpls)# key size limit 160
switch(config-tcam-feature-pbr-mpls)# key field mpls-inner-ip-tos
switch(config-tcam-feature-pbr-mpls)# action count drop redirect
switch(config-tcam-feature-pbr-mpls)# packet mpls ipv4 forwarding mpls
switch(config-tcam-feature-pbr-mpls)# packet mpls ipv6 forwarding mpls
switch(config-tcam-feature-pbr-mpls)# packet mpls non-ip forwarding mpls
switch(config-tcam-feature-pbr-mpls)# exit
switch(config-tcam-profile-traffic-policy)# feature qos ip
switch(config-tcam-feature-qos-ip)# sequence 75
switch(config-tcam-feature-qos-ip)# key size limit 160
switch(config-tcam-feature-qos-ip)# key field dscp dst-ip ip-frag ip-protocol l4-dst-port l4-ops l4-src-port src-ip tckp-control
switch(config-tcam-feature-qos-ip)# action set-dscp set-policer set-tc
switch(config-tcam-feature-qos-ip)# packet ipv4 forwarding routed
switch(config-tcam-feature-qos-ip)# packet ipv4 forwarding routed multicast
switch(config-tcam-feature-qos-ip)# packet ipv4 mpls ipv4 forwarding mpls decap
switch(config-tcam-feature-qos-ip)# packet ipv4 mpls ipv6 forwarding mpls decap
switch(config-tcam-feature-qos-ip)# packet ipv4 non-VXLAN forwarding routed decap
switch(config-tcam-feature-qos-ip)# exit
switch(config-tcam-profile-traffic-policy)# feature qos ipv6
switch(config-tcam-feature-qos-ipv6)# sequence 70
switch(config-tcam-feature-qos-ipv6)# key field dst-ipv6 ipv6-next-header ipv6-traffic-class l4-dst-port l4-src-port src-ipv6-high src-ipv6-low
switch(config-tcam-feature-qos-ipv6)# action set-dscp set-policer set-tc
switch(config-tcam-feature-qos-ipv6)# packet ipv6 forwarding routed
switch(config-tcam-feature-qos-ipv6)# exit
switch(config-tcam-profile-traffic-policy)# feature traffic-policy port ipv4
switch(config-tcam-feature-traffic-policy-port-ipv4)# sequence 45
switch(config-tcam-feature-traffic-policy-port-ipv4)# key size limit 160
switch(config-tcam-feature-traffic-policy-port-ipv4)# key field dscp dst-ip-label icmp-type-code ip-frag ip-fragment-offset ip-length ip-protocol l4-dst-port
switch(config-tcam-feature-traffic-policy-port-ipv4)# l4-src-port src-ip-label tcp-control ttl
switch(config-tcam-feature-traffic-policy-port-ipv4)# action count drop log set-dscp set-tc
switch(config-tcam-feature-traffic-policy-port-ipv4)# packet ipv4 forwarding routed
switch(config-tcam-feature-traffic-policy-port-ipv4)# exit
switch(config-tcam-profile-traffic-policy)# feature traffic-policy port ipv6
switch(config-tcam-feature-traffic-policy-port-ipv6)# sequence 25
switch(config-tcam-feature-traffic-policy-port-ipv6)# key field dst-ipv6-label hop-limit icmp-type-code ipv6-length ipv6-next-header ipv6-traffic-class l4-dst-port
switch(config-tcam-feature-traffic-policy-port-ipv6)# l4-src-port src-ipv6-label tcp-control
switch(config-tcam-feature-traffic-policy-port-ipv6)# action count drop log set-dscp set-tc
switch(config-tcam-feature-traffic-policy-port-ipv6)# packet ipv6 forwarding routed
switch(config-tcam-feature-traffic-policy-port-ipv6)# exit
switch(config-tcam-profile-traffic-policy)# feature tunnel vxlan
switch(config-tcam-feature-vxlan-tunnel)# sequence 50
switch(config-tcam-feature-vxlan-tunnel)# key size limit 160
switch(config-tcam-feature-vxlan-tunnel)# packet ipv4 VXLAN eth ipv4 forwarding routed decap
switch(config-tcam-feature-vxlan-tunnel)# packet ipv4 VXLAN forwarding bridged decap
switch(config-tcam-feature-vxlan-tunnel)# exit
switch(config-tcam-profile-traffic-policy)#