There are a number of wireless threat vectors that network managers need to defend against. One of the more common types of threats to WLANs is from rogue APs. An analysis of Wireless Intrusion Prevention Systems (WIPS) that are available today reveals that many require a high level of administration and often provide less-than-trustworthy rogue AP detection. Organizations that depend on these less capable systems often have a false sense of security as their networks are in fact vulnerable to breaches via rogue APs. Less capable WIPS are also prone to raising false alarms, which can lead administrators to ignore alerts or turn notifications off altogether, leaving their organizations unprotected. In contrast to competing WIPS offerings, the industry leading solution from Arista Networks requires a minimal amount of management overhead while providing reliable rogue AP detection and prevention.
Rogue Access Points
Rogue APs can be defined as any unauthorized AP that is connected to an authorized network. Rogue APs can appear on the enterprise network either due to naïve acts of employees or due to malicious attempts by insiders. Rogue APs are a serious threat to enterprise networks as they allow unauthorized wireless access to the private network and data, as shown in the diagram below.
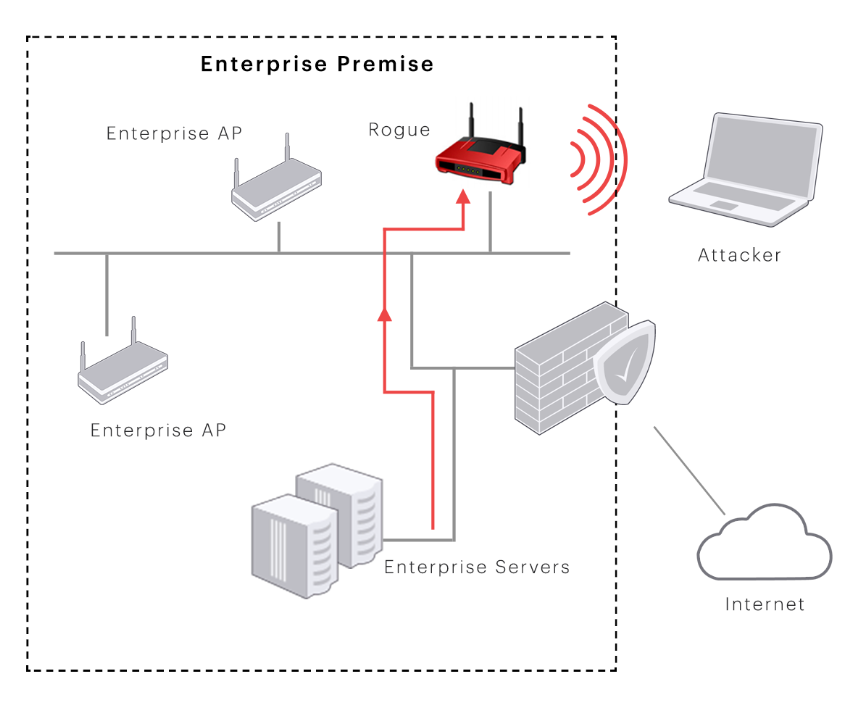
Rogue AP detection approaches
A naïve way to detect rogue APs in the LAN is to declare every AP seen in the air that does not belong to the list of authorized APs as rogue. In fact, many WIPS available in the market will actually follow this approach, by default. Such an approach has the following disadvantages:
- False alarms: A security alert would be raised even if the non-authorized AP seen in the air but not actually connected to the monitored wired network and as such it does not pose any security threat
- Manual intervention:The system administrator has to manually examine the non-authorized APs visible in the air to decide which of them are actual rogue APs and which of them are external APs (i.e. neighbor APs).
- No automatic instantaneous prevention: Since it is highly undesirable to block neighbors' APs accidentally or indiscriminately, instantaneous and automatic blocking of rogue APs is not possible with such an approach.
Arista Approach
Using Arista's patented Marker Packet™ techniques, Arista Wireless Intrusion Prevention System (WIPS) automatically and quickly classifies wireless devices detected in the airspace as Authorized, Rogue and External. As a result, security administrators do not need to manually inspect devices or define complex rules to identify rogue wireless devices. This is better than the error-prone device classification integrated into most other WLAN solutions, which relies on slow and inconclusive CAM table lookups and MAC correlation, signatures, or passive wired network sniffing.
Arista WIPS focuses on the primary threat vectors and vulnerabilities that form the building blocks for all known and emerging Wi-Fi hacking attacks and tools. It offers comprehensive protection from all types of wireless threats, including Rogue APs, Soft APs, Honeypots, Wi-Fi DoS, Ad-hoc networks, Client misassociation, and Mobile hotspots.
Highlighted capabilities
- Automatically detects, blocks and locates all types of wireless threats
- Patented Marker Packet&trade techniques eliminate false alarms in 'on wire' Rogue AP detection
- Secure BYOD policy enforcement
- Off-line sensor mode for fault tolerant continuous policy enforcement
- Detects and locates 'non Wi-Fi' interference & RF jamming
- Remote troubleshooting including remote 'live packet capture'
- Management options include virtual server or cloud
